In the ever-evolving cybersecurity landscape, robust intrusion detection and prevention systems (IDS/IPS) play a critical role in safeguarding networks. Snort emerges as a widely deployed open-source IDS/IPS, offering comprehensive network traffic analysis and threat detection capabilities. This blog post delves into the intricate workings of Snort, exploring its internal components, engines, and the exciting potential of integrating it with AI models for enhanced threat detection.
Snort: A Multifaceted Network Guardian
Snort operates in two primary modes:
- Intrusion Detection System (IDS): In this mode, Snort meticulously monitors network traffic for suspicious activity based on predefined rules. When a potential threat is identified, Snort generates alerts, notifying security professionals for further investigation.
- Intrusion Prevention System (IPS): This mode elevates Snort’s capabilities beyond detection. When a rule match indicates a potential attack, Snort actively prevents the threat by dropping packets, resetting connections, or taking other predefined actions to thwart the attacker.
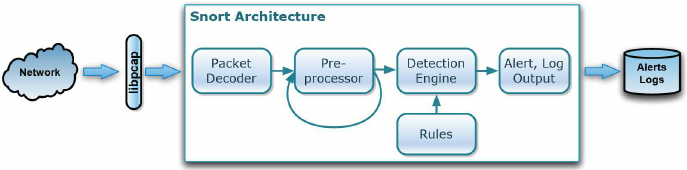
The Engine Room of Snort: Powering Network Protection
Snort leverages a collection of powerful engines to dissect network traffic and identify potential threats:
- Preprocessor Engine: This engine acts as the first line of defense. It efficiently parses network packet headers, extracting crucial information for further analysis.
- Detection Engine: The heart of Snort, the detection engine meticulously compares the extracted packet data against a predefined rule set. These rules encompass patterns associated with known attacks, vulnerabilities, and suspicious network activity.
- Classification Engine (Optional): This engine provides an additional layer of analysis, categorizing detected threats based on severity and potential impact.
- Output Engine: The output engine takes center stage when a rule match occurs. It generates alerts, logs events, or triggers predefined actions based on the configured mode (IDS or IPS).
- Packet Decoder Engine (Optional): For deeper analysis, Snort can leverage a packet decoder engine to dissect the payload of suspicious packets, revealing potential malicious content.
Rule Sets: The Backbone of Threat Detection
Snort’s effectiveness hinges on a comprehensive and up-to-date rule set. These rules define the patterns and characteristics Snort searches for within network traffic. Commonly used rule sets include:
- Community Rules: A vast collection of community-developed rules, offering broad threat coverage.
- Vendor Rules: Commercial security vendors offer rule sets tailored to specific threats and vulnerabilities.
- Custom Rules: Security teams can create custom rules to address unique threats or vulnerabilities within their network environment.
The Rise of AI in Intrusion Detection: Empowering Snort
The integration of AI models with Snort unlocks exciting possibilities for enhanced threat detection. Here are some ways AI can augment Snort’s capabilities:
- Automated Rule Generation: AI models can analyze network traffic data and automatically generate new rules to identify emerging threats and zero-day vulnerabilities.
- Adaptive Threat Detection: AI can continuously learn and adapt to evolving attack patterns, ensuring Snort’s rules remain relevant and effective against the latest threats.
- Anomaly Detection: AI-powered anomaly detection models can analyze traffic patterns to identify deviations from normal behavior, potentially uncovering novel or subtle attacks that traditional rule-based detection might miss.
Integrating AI with Snort: A Glimpse into the Future
Several approaches exist for integrating AI with Snort:
- Preprocessing: AI models can be used to pre-process network traffic data, identifying suspicious elements before feeding the data into Snort’s detection engine for further analysis.
- Rule Scoring: AI can analyze rule matches and assign a risk score based on the context and potential impact, enabling security teams to prioritize investigation efforts.
- Alert Correlation: AI can correlate alerts from Snort with other security tools, identifying potential coordinated attacks and providing a more comprehensive view of the security landscape.
The Future of Network Security: A Collaborative Approach
Snort, with its multifaceted engines, comprehensive rule sets, and the potential for AI integration, offers a powerful foundation for network security. By leveraging AI’s capabilities, Snort can evolve beyond traditional rule-based detection, enabling security teams to proactively combat emerging threats and safeguard their networks with exceptional efficiency.
Stay tuned for our next blog post, where we’ll delve deeper into the practical implementation of AI models with Snort, exploring specific use cases and configuration considerations to empower your network security posture.